Resources
Endera Unveils Next-Generation Continuous Evaluation Platform for Workforce Risk Management
Endera’s new CE platform transforms workforce risk management with advanced identity solutions, compliance tools and Zero…
Redefining Cybersecurity: 2023's Major Data Breaches CATAPULTS US TO ZERO TRUST ARCHITECTURE (zta) IN 2024 AND BEYOND
In the ever-evolving domain of cybersecurity, the year 2023 will be etched in memory as a…
Remote Workforce Causing Headaches - There's an Aspirin for that
Remote Workforce Causing Headaches – There’s an Aspirin for that Recently, J.P. Morgan hosted Screener Day,…
High Risk Threat Signals - Easy ROI with High Knowledge and Low Effort
High Risk Threat Signals – Easy ROI with High Knowledge and Low Effort The cybersecurity landscape…
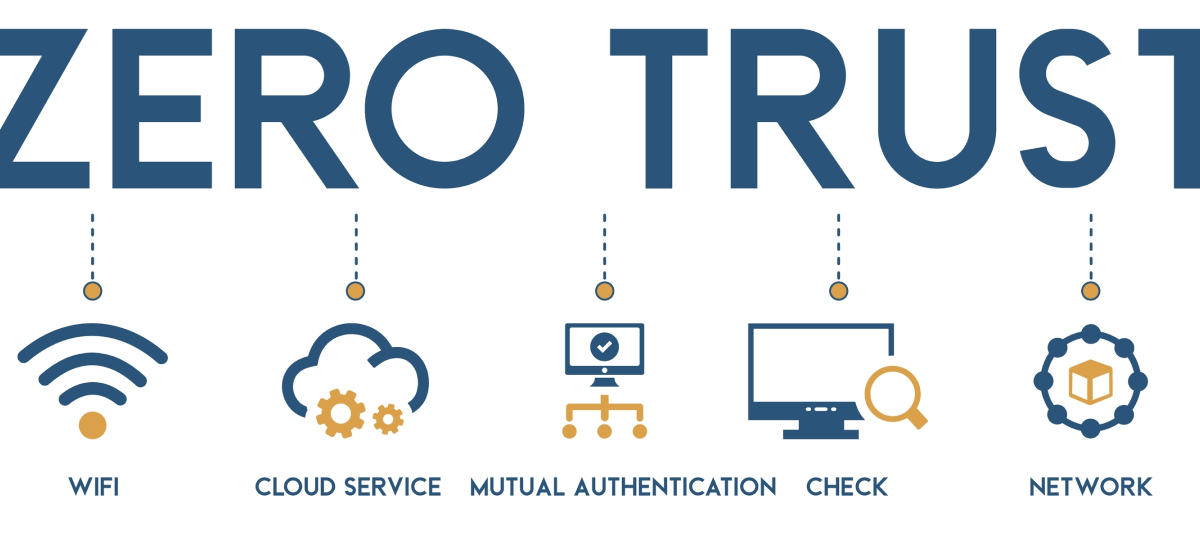
Architectural Drawing - Zero Trust Architecture Part Two
Architectural Drawing – Zero Trust Architecture Part Two In the first part of our deep dive…
Enhancing Security with Zero Trust Architecture: Part One - Trust Redefined
In this two-part series, we’ll dive deep into the concept of Zero Trust Architecture (ZTA) and…
Mitigating Supply Chain Risks with Continuous Evaluation
Mitigating Supply Chain Risks with Continuous Evaluation In the current globalized business environment, supply chains extend…
External Signals – A missing Gap in Insider Threat Programs
External Signals – A missing Gap in Insider Threat programs In the realm of corporate security,…
Unveiling the Key to Successful Post M&A Security: The Solution You've Been Seeking
Unveiling the Key to Successful Post M&A Security: The Solution You’ve Been Seeking Picture this: You,…
The Key to Proactive Security: Unlocking the Power of Continuous Evaluation
Today’s digital threats are evolving at an unprecedented pace. With insider threats on the rise, security…