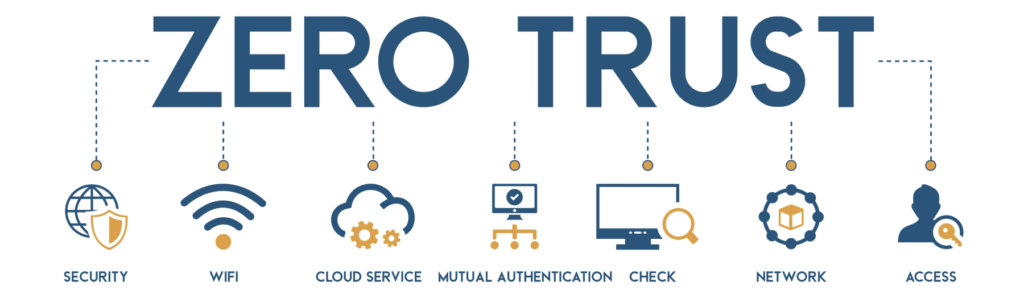
In this two-part series, we’ll dive deep into the concept of Zero Trust Architecture (ZTA) and its implications for enhancing security. We’ll discuss the limitations of outdated trust models and the need for a more dynamic approach. Together, we’ll unravel the potential risks associated with background screenings that are out of date, shedding light on the blind spots in security.
In today’s rapidly evolving digital landscape, traditional security approaches that rely on trusting the network are no longer sufficient. The rise of Zero Trust Architecture (ZTA) has introduced a paradigm shift, placing the focus on users rather than the network itself. By embracing the principle of least privilege, ZTA advocates for a comprehensive and dynamic evaluation of trust, mitigating potential risks and enhancing overall security. In this article, we delve deeper into the concept of ZTA and explore its significance in addressing the gaps that exist in user verification within organizations.
Redefining Trust in the Digital Age:
While organizations have access to various tools that support continuous validation, there are still critical gaps in understanding the user. ZTA prompts us to question the factors that should influence the level of trust granted to a user at any given time. Consider scenarios where access to sensitive financial data is being considered for a user who has recently been arrested for theft. This raises the need for organizations to move beyond one-time background checks and adopt a more dynamic approach to trust evaluation.
Moving Away from Outdated Trust Models:
The heart of the issue lies in the disconnection between HR and security departments. Organizations often treat background checks as a one-time process, assuming that trust remains unchanged thereafter. However, ZTA challenges this approach by highlighting the importance of continuous evaluation and contextual risk assessment. By connecting HR data and security measures, organizations can reassess trust levels based on real-time information, identifying potential risks originating from external signals of insiders.
Embracing the Proactive Stance of Zero Trust:
ZTA extends beyond the traditional notion of monitoring user behavior for irregularities. It emphasizes the identification of risk elements that can originate externally, such as recent criminal activities or suspicious behaviors. By taking a proactive stance, organizations can mitigate potential threats that may not be immediately apparent through internal monitoring alone. This capability shouldn’t be limited to financial institutions alone; critical infrastructure operators, custodians of medical records, and other organizations must also implement similar measures.
The Advantages of Zero Trust Architecture:
Implementing ZTA empowers organizations to establish a robust security framework that aligns with the evolving threat landscape. It encourages a holistic understanding of user trustworthiness, enabling more informed access control decisions. By continuously assessing risks and evaluating relevant external factors, ZTA ensures that access privileges are consistently aligned with the current risk profile of users. This dynamic approach enhances security posture and safeguards critical assets.
Zero Trust Architecture (ZTA) represents a fundamental shift in security strategies, placing users at the forefront and redefining the concept of trust. By moving beyond traditional trust models and adopting a continuous evaluation approach, organizations can better address vulnerabilities and mitigate potential risks. ZTA empowers organizations to proactively identify and respond to external threats while maintaining a secure network infrastructure. By embracing the principles of ZTA, organizations can enhance their security posture and build a robust defense against the ever-evolving threat landscape of the digital age.
Stay tuned for Part Two – “The Blind Spot in Security,” we’ll unveil the potential vulnerabilities that arise when trust is based on historical data alone, and we explore effective strategies to mitigate workforce risk.