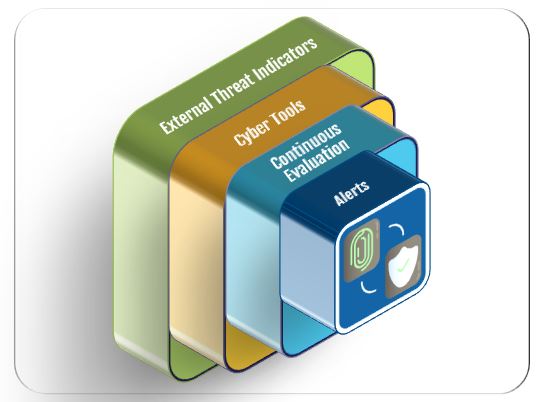
In the ever-evolving domain of cybersecurity, the year 2023 will be etched in memory as a landmark era marked by unprecedented challenges and transformative lessons. The digital realm, once considered a frontier of limitless possibilities, has increasingly become a battleground for data integrity and privacy. Within this context, a multi-layered cybersecurity framework has emerged as an essential lens through which to scrutinize and understand these internal breaches. The model of external threat indicators, cyber tools, continuous evaluation, and alerts does not merely serve as a passive backdrop; it becomes a critical vantage point from which we can dissect the year’s tumultuous events.
As we cast our eyes back on the tumultuous landscape of cybersecurity in 2023, we are reminded of a year punctuated by relentless challenges and high-profile data breaches. It was a year that saw the menacing specter of insider threats continue to loom large, prompting us to reassess and recalibrate our strategies for the future. Let’s journey back and examine two particularly notorious data breaches at leading companies – People Connect, Luxottica, and Kodi. Each of these incidents was masterminded by a solitary figure lurking within the network, sending shockwaves through the industry and making headlines worldwide.
Imagine this – a single individual, hidden behind the veil of anonymity, pulls off a massive data breach, putting the personal information of over 20 million people in jeopardy. That’s exactly what happened with People Connect, a company whose subsidiaries include Instant Checkmate and TruthFinder. This wasn’t a random attack from the outside – it was an inside job, a shocking betrayal that sent shockwaves through the company and its users. The culprit? Still unknown. The method? Likely the dark web, a shadowy, invite-only corner of the internet. This incident is a chilling reminder of the importance of robust cybersecurity measures, and how a single insider can wreak havoc on a grand scale. It’s a wake-up call to all businesses – the threat can come from within, and it’s crucial to be prepared.
The 2023 Luxottica data breach, which had actually occurred two years prior, exposed the personal information of a staggering 70 million customers due to a vulnerability in their data supply chain. A hacker forum boasted a database claiming to hold the records of 300 million Luxottica customers from the US and Canada, which was later confirmed to be accurate. The breach was not a direct attack on Luxottica’s systems, but rather a result of a compromised partner network, revealing the inherent vulnerabilities in the interconnected data supply chains of large corporations. Luxottica’s vast collection of personal data, including sensitive medical histories, presented an attractive target for cybercriminals. This delay in confirming the breach highlighted the urgent need for enhanced security protocols and continuous vigilance across all supply chain partners. The Luxottica breach serves as a stark reminder that supply chains can become channels of exploitation if not properly secured, especially when handling sensitive health and other personal information.
In the People Connect breach, a severe internal data leak where sensitive information of over 20 million individuals was compromised. The leaked data, originating from a 2019 backup database, included personal details of Instant Checkmate and TruthFinder subscribers such as names, emails, phone numbers, hashed passwords, and old password reset tokens. Upon investigation, it was revealed that the breach was an inside job, suggesting a lone wolf either sold the information or had access to the dark net. Despite speculation of an accidental leak, the possibility was ruled out due to the exclusive nature of the dark web, which requires an invitation from an existing user for access. The breach was confined to People Connect’s subsidiaries, a small miracle considering the company’s complex ownership structure involving Intelius and H.I.G. Capitol. The security response team, despite their best efforts, hit a dead end in their investigation, unable to pinpoint the individual responsible for the breach. The incident underscored the chilling reality of a threat originating from within, leaving the team grappling with the enormity of their task and the stark vulnerability of the data they were entrusted to protect.
These incidents highlight the complex and interconnected nature of today’s cybersecurity challenges, underscoring the fact that a single individual within a network can cause significant damage to a brand’s reputation and security. This not only exposes the organization’s vulnerabilities but also erodes trust in the security teams tasked with its protection. The risks posed by insiders are significant, as they can inflict deep and lasting damage on an organization’s reputation, customer trust, and overall security. Given this, it’s clear that the security response teams need better tools to address these threats. In light of these events, one can’t help but wonder: what could they have done differently? This question will guide our exploration of future planning and tactics to mitigate against these threats.
Examining major breaches with a focus on data supply chain vulnerability exposes a significant flaw in contemporary cybersecurity structures. The Luxottica case, where a partner network was compromised, is a clear example of this. This demonstrates the limitations of perimeter defense strategies, as they often only extend to the corporation’s boundaries, leaving partner networks vulnerable. The interconnectedness in data supply chains can be exploited, leading to far-reaching consequences.
The increasing sophistication of cyberattacks, the rise of remote work and digital transformation, regulatory pressures, and the interconnectedness of systems necessitate a more comprehensive approach to cybersecurity. This approach must extend beyond the main organization to its entire network of partners and suppliers, despite the challenges posed by partners operating outside of the organization’s environment. It must integrate advanced threat detection, robust data encryption, proactive threat intelligence, and deeper verification and monitoring across dispersed networks. The stakes for security teams have never been higher, due to potential financial penalties and reputational damage resulting from breaches, and the far-reaching impacts of breaches on business operations. These factors collectively highlight the urgent need for a continuously evolving, holistic cybersecurity strategy.
As we look ahead to the cybersecurity landscape of 2024, it’s clear that many organizations are facing a critical juncture. Despite having a suite of tools and strategies at their disposal, they remain woefully inadequate in the face of the rapid advancements in technology and the expansion of their digital footprint. The reality is, that the gap between the capabilities of current security measures and the ingenuity of cybercriminals is poised to widen. To overcome this, a paradigm shift is required. Organizations must move towards a more advanced, integrated, and adaptive cybersecurity strategy, one that focuses on the person on the network, rather than just the boundary. This is not just an upgrade, but a revolution in how we approach cybersecurity.
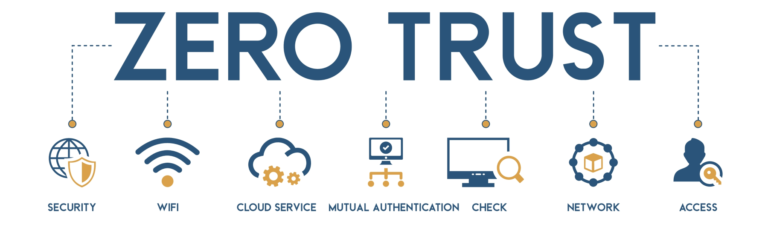
The ascent of Zero Trust Architecture (ZTA) in the cybersecurity landscape is increasingly recognized as a critical strategy to combat evolving threats. Central to ZTA’s effectiveness is its dynamic integration of data about trusted individuals into access, incident, and response systems. This approach fundamentally shifts from traditional perimeter-based defenses to a model where trust is never assumed and always verified, regardless of whether the threat originates from outside or within the organization. By continuously analyzing user behavior and context, ZTA adapts access controls and privileges in real-time, enhancing security against both external and internal threats. This data-centric, adaptive framework enables quicker, more precise responses to security incidents, positioning ZTA as a pivotal solution in addressing the complex cybersecurity challenges of today.
Continuous evaluation, integral to the Zero Trust Architecture (ZTA), is a dynamic cybersecurity process that constantly assesses the backgrounds and behaviors of individuals accessing an organization’s systems. This ongoing scrutiny is a crucial enhancement to traditional ZTA tools, which typically focus on immediate network behaviors and access requests. Continuous evaluation transcends these immediate signals by proactively adjusting user risk profiles and access privileges in real-time, based on observed actions. This approach not only responds to but anticipates potential security risks, ensuring swift identification and mitigation of anomalous behavior. By embedding continuous evaluation into the ZTA framework, organizations can fortify their defenses against both external and internal threats, creating a more nuanced, responsive, and robust cybersecurity environment. Don’t wait for the next headline-making breach to reassess your cybersecurity strategy. Take a proactive step towards fortifying your defenses now. Contact us today to learn more about Continuous Evaluation and how it can revolutionize your security approach. Discover how this dynamic process, integral to Zero Trust Architecture, can provide a more nuanced, responsive, and robust cybersecurity environment for your organization. Experience firsthand how continuous evaluation can anticipate potential security risks, ensuring swift identification and mitigation of anomalous behavior. Let us show you how to turn your cybersecurity from a vulnerability into a strength. Don’t just react to threats – anticipate them. Contact us now for a demonstration. Your security can’t wait.