High Risk Threat Signals – Easy ROI with High Knowledge and Low Effort
The cybersecurity landscape has evolved significantly, transforming from an IT concern to a strategic business discussion. However, one challenge remains: how do we effectively articulate security investments to other business stakeholders? The answer might surprise you. Instead of presenting in terms of threats and vulnerabilities, let’s approach this through a lens they understand well – Return on Investment (ROI).
Imagine a graph, with two axes: ‘Level of Effort’ on the vertical and ‘Level of Knowledge’ on the horizontal. This creates four distinct quadrants, each representing different ROI scenarios for security investments.
Let’s walk through the four quadrants of this graph to consider the tools and methods that are investments of the enterprise. Looking through the lens of ROI, we can run security like we run the business.
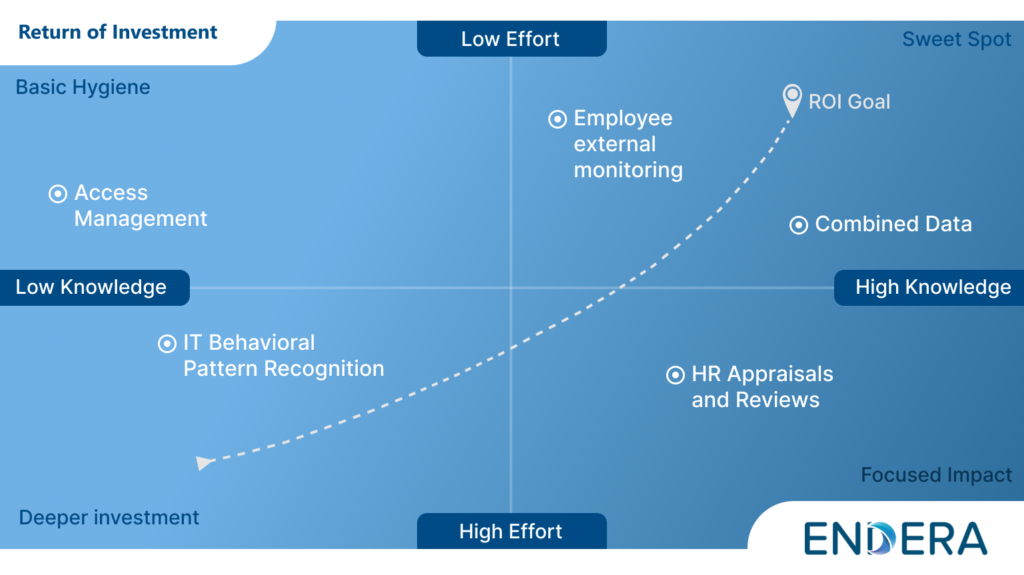
1. Low Effort, Low Knowledge (Basic Hygiene):
Example: Access Control
In the world of enterprise security, access control stands as a quintessential ‘lock on the front door.’ It’s a primary layer of defense, offering foundational measures that require minimal effort and basic knowledge. The immediate ROI is clear: it curtails unauthorized access, ensuring only the right individuals have entry to our precious data troves and critical resources.
However, in recent years, many have touted the merits of a Zero Trust Architecture. But let’s take a moment to reflect. Isn’t the essence of Zero Trust, in its true form, contrary to the realm of low effort and low knowledge?
For the sake of argument, imagine we are equipping our home with security. Basic access control would be the front door lock. While it’s necessary, would you rely solely on it, knowing there are other potential entry points or more sophisticated threats that a basic lock can’t deter?
Similarly, while access control forms an integral part of our cybersecurity fabric, it’s a simplistic measure. By itself, it lacks the depth and sophistication needed to confront the multifaceted challenges of today’s cyber realm. Zero Trust, on the other hand, goes beyond merely locking the door. It scrutinizes every individual, every request, and every action – challenging our initial placement of access control in the ‘low knowledge’ quadrant.
Can tools, even those labeled as ‘Zero Trust,’ truly be effective if they’re implemented with only basic knowledge and in isolation? Or do they require a deeper effort to truly deliver on their promise? Let’s consider the next quadrant as being the investments where a deeper level of effort is required.
2. High Effort, Low Knowledge (Deeper Investments):
Example: Behavioral Pattern Recognition
Imagine investing in an advanced home security system, complete with motion sensors, surveillance cameras, and alarms. Yet, each time a leaf flutters by or a cat scurries across your garden, the alarms blare, causing disturbances and unnecessary panic. You’ve invested heavily, but the return? A myriad of false positives. This scenario draws a parallel with certain cybersecurity measures like behavioral pattern recognition when applied superficially.
The promise of behavioral pattern recognition is tantalizing: the idea of preempting threats based on anomalies in behavior patterns. Can high effort tools like User Behavior Analytics and internal network traffic data, laden with the best of technological advancements, truly maximize their potential if they operate on limited or superficial knowledge?
When behavioral pattern recognition tools are deployed without the requisite depth of knowledge – essentially relying on rudimentary parameters – the result is akin to our oversensitive home alarm. They end up demanding enormous efforts in terms of manual reviews, adjustments, and fine-tuning. But the returns? Often, a barrage of false positives drains resources and leads to ‘alert fatigue.’
If we’re investing heavily in such tools, wouldn’t we want them to discriminate between genuine threats and benign activities with precision? Is it not counterproductive to have an advanced system that, for lack of deeper understanding, treats every deviation as a potential threat? And so, the paradox emerges: tools that are high on effort but operate on low knowledge can quickly transition from being assets to liabilities, diminishing their ROI. The problem here is that the effort is focused on the behavior without the context of the person performing the behavior. Let’s consider how most organizations focus on the knowledge of the individual.
3. High Effort, High Knowledge (Focused, but Limited Impact):
Example: HR Appraisals and Reviews
Visualize a renowned research facility with multiple labs, each housing an expert dedicated to their unique field of study. These experts produce groundbreaking findings daily. Yet, there’s a catch: these researchers never share their discoveries with each other. Each lab becomes an island of knowledge, rich in insights but limited in collaborative potential.
Such is the nature of HR appraisals and reviews when viewed from an organizational perspective. Deep, meticulous, and insightful, these processes delve into the intricacies of individual performance and potential threats therein. However, when confined within the silos of HR departments, much of this rich knowledge remains untapped in the broader security context.
If vital information about individual behaviors, potential threats, and vulnerabilities stays trapped within HR’s domain, aren’t we missing an opportunity? Is it efficient to accumulate such profound insights but restrict their application to mere job performance, overlooking their value in enhancing security?
This siloed approach parallels the isolated labs: vast knowledge, high effort, but limited overarching impact. While HR appraisals can detect anomalies or potential insider threats, their ROI in the broader security landscape is diluted when not integrated with the organization’s wider security strategies.
In an era where collaboration is key, where knowledge-sharing forms the backbone of innovation, should we not extend this ethos to our security posture? Would not the cross-pollination of insights from HR reviews with the broader security strategy fortify our defenses? Shouldn’t we perform recurrent or continuous screening of our workforce for relevant threats to the organization?
If we want to run security like a business, we must break down these organizational silos. While high-knowledge, high-effort processes like HR reviews are invaluable, their true potential is realized only when their insights are shared, integrated, and acted upon in the broader security context. It’s in this integration that we transform isolated knowledge pockets into a cohesive, formidable shield against threats.
4. Low Effort, High Knowledge (The Sweet Spot):
We now arrive at an answer to our posed dilemmas. Can there be a space where knowledge is vast and yet the effort required is not overwhelming? Is there a way to integrate insights from different domains, transcend silos, and achieve a security posture that’s both wide-reaching and efficient?
Welcome to the Sweet Spot of high ROI.
In a rapidly evolving digital landscape, static defenses or sporadic evaluations are not just inadequate; they can be detrimental, leading to false complacency. What enterprises require is dynamic, continuous evaluation—a system tool that offers a fluid, ongoing insight into potential risks.
By focusing on monitoring ‘ workforces’ relevant external threat signals, we harness powerful insights indicative of risk. Such activity might include, DUIs detrimental to the organization, domestic violence issues that could spill into the workplace, sex offender registries, criminal convictions, or engagement with entities that raise red flags. These aren’t just random data points; they are a goldmine of context, enhancing the depth and breadth of our knowledge.
This continuous evaluation approach is transformative. Instead of isolated snapshots of potential risks, we gain a rolling film, capturing trends, anomalies, and patterns in real time. This not only provides instantaneous alerts but also offers a historical context, vital for understanding the evolution of potential threats.
In simple terms, while other tools might tell us ‘what’ is happening, continuous evaluation provides the ‘why’—the context that underpins deeper knowledge. This is the embodiment of ROI in security. It’s a method that requires comparatively lower effort, thanks to automation, yet delivers a depth of understanding that’s unparalleled.
For organizations looking to fortify their defenses while maximizing ROI, the path is clear: integrate tools and strategies that provide ongoing, dynamic insights into potential threats. Pair this with the intelligence gleaned from other quadrants, and the result is a comprehensive, ROI-centric security strategy.
So, what’s our takeaway?
In the vast expanse of enterprise security, the myriad tools and methodologies we employ are not just about fortifying digital fortresses. They symbolize investments – capital, time, and intellectual prowess. And like any astute business leader, we ought to discern the value and potential returns of these investments.
Our journey through the four quadrants of effort and knowledge brings to the forefront a crucial lesson: Security, at its core, is an intricate dance of balancing knowledge depth with effort optimization. And it’s not just about countering threats; it’s about ensuring every resource, every tool, and every strategy is harnessed to its maximum potential to provide optimum ROI. Every business decision, including those in cybersecurity, must be rooted in discerning value, anticipating returns, and judicious allocation of resources. We began with a simple premise: run security like we run a business. And the conclusions are resounding. It’s not about more; it’s about more effective. It’s not about complexity; it’s about sophistication. And most crucially, it’s not just about defense but intelligent, ROI-driven defense.